In the age of high-profile corporate data breaches (check out that top 10 list if you don’t want to sleep tonight), many WAN managers have security on their minds. Traditionally, enterprises treated their network security like a fortress, creating strong defenses at the perimeters of the network to defend the data and resources inside.
However, folks are realizing that all the defenses in the world will do you little good when the bad guy has the keys to the kingdom. According to Verizon’s 2017 Data Breach Investigation Report, more than 80% of breaches stemmed from stolen or weak passwords.
At the same time, the increasing migration to cloud applications, the rise of remote and BYOD users, and the addition of local internet breakouts have introduced new security vulnerabilities to the network.
As such, network professionals are starting to shift their mindset from static, perimeter-based security to a user-focused security paradigm. This evolving security philosophy, coined Zero Trust Security for its “never trust, always verify” mindset, has become a hot-button issue.
As such, network professionals are starting to shift their mindset from static, perimeter-based security to a user-focused security paradigm. This evolving security philosophy, coined Zero Trust Security (ZTS) for its “never trust, always verify” mindset, has become a hot-button issue.
In this post we’ll be taking a look at how WAN managers are approaching ZTS in their own networks, pulling from the new security section of our WAN Manager Survey.
Where Are WAN Managers in Their ZTS Adoption?
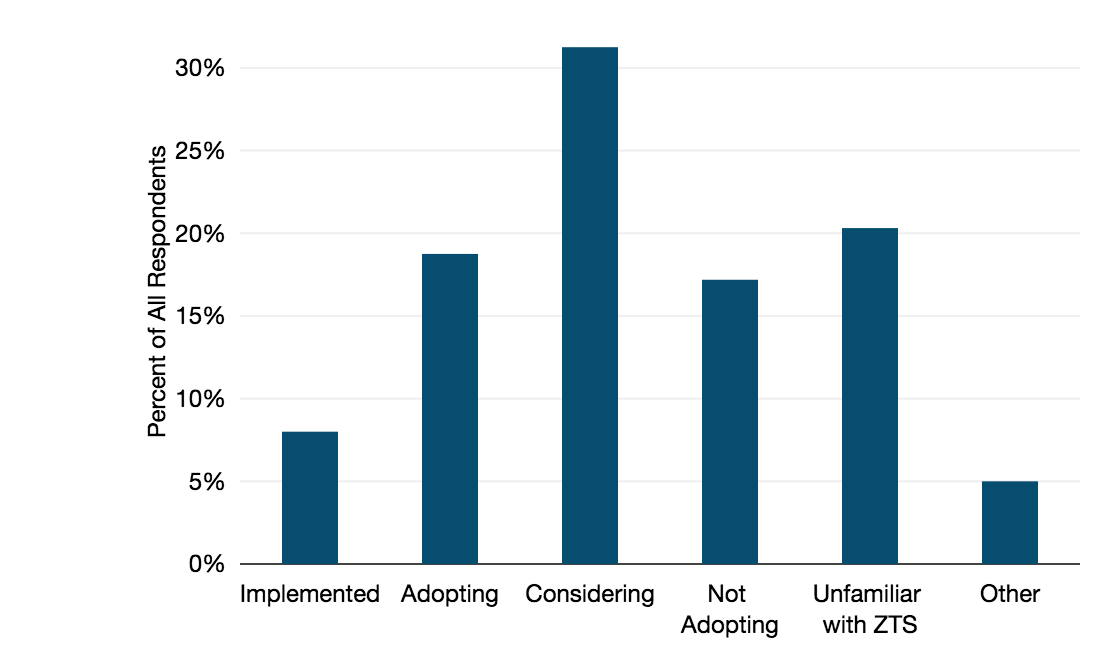
Interest in the ZTS model is high, but few have made the leap into implementation.
Half of participating WAN managers were at some stage of considering or adopting ZTS. But only 8% had actually implemented it on some part of their network.
A sizable group, 17%, evaluated ZTS and decided against implementation.
One in five respondents took a look at the question and went, “What the heck is ZTS?” (I hope anyone who picked this response is finding answers in this blog.)
What are your plans for adopting ZTS?
Besides the information gap, WAN managers face real challenges in configuring legacy systems into a structure that works with zero trust principles.
To have user-based or device-based authentication, every user and device on the network must be identified and tracked first. For many, that’s a huge undertaking. It might include networks that cross borders and cover thousands of employees.
Micro-segmentation also requires an understanding of where sensitive data is stored and how it flows through the network—and potentially redesigning where data sits. Some networks may have sensitive and non-sensitive data siloed together, with access granted based on the silo, not the data. This needs to be corrected to manage access privilege.
Also, companies are often going through other digital transformation or tech deployments at the same time as a ZTS roll-out. To keep up with data storage and access management in a dynamic business environment, some level of automation may be required rather than manual granting of access.
Several survey interviewees predicted at least a three to five-year roll-out window needed for ZTS, considering the preparation needed in advance. Others were more pessimistic, saying that greater levels of automation and big data processing technology would first need to be adopted to realistically deploy ZTS.
Zero Trust Security Features
We also wanted to see what features were motivating companies to move toward ZTS adoption.
The National Institute of Standards and Technology recently released a working paper that defined the main goals of zero trust architecture as (1) blocking any and all unauthorized access to data and services and (2) establishing granular access policies for all users and devices.
To achieve those goals, the ZTS model focused on verifying users, validating devices, limiting access and privileges, and using analytics to adapt policies.
What features are key drivers for you to adopt ZTS?
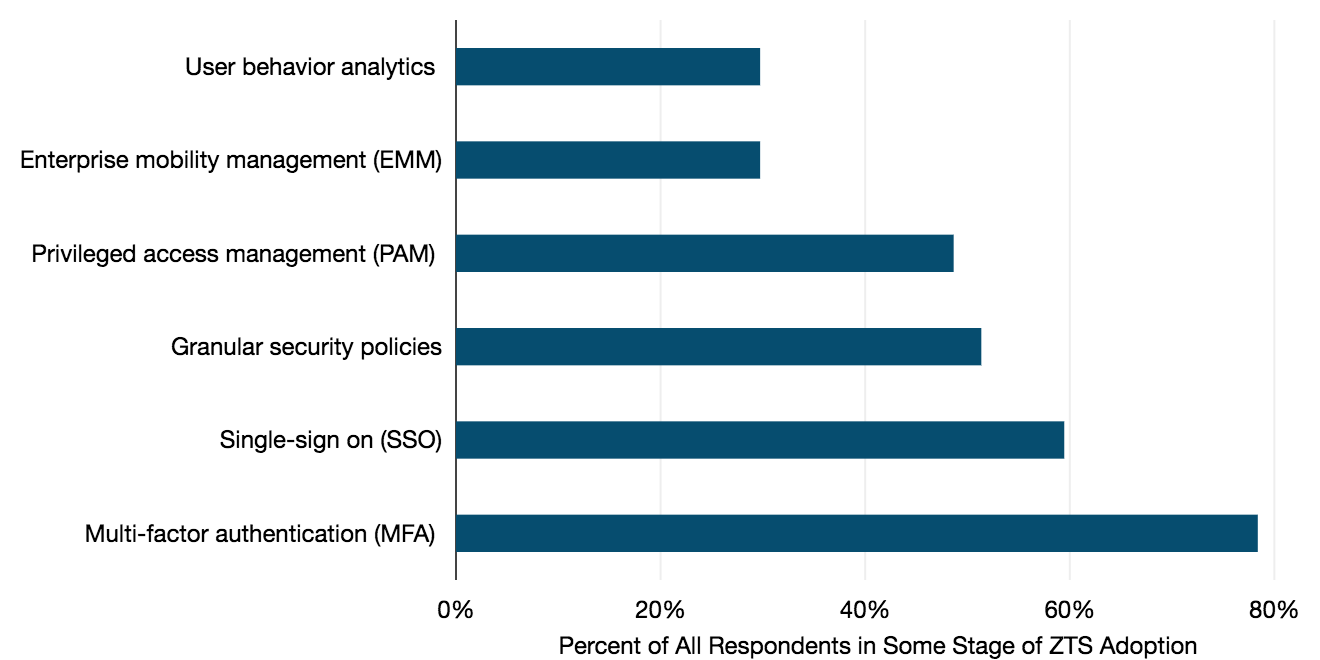
Among WAN managers who were in some stage of adopting or considering ZTS, strengthening user credentials with multiple factors of authentication—known as multi-factor authentication or MFA—and single sign-on held the strongest appeal.
The ability to manage user privileges and set granular security policies were also selected by around half of respondents.
Zero trust is a set of interlocking security strategies, not a single product. So we also wanted to see how enterprises approach their sourcing of security vendors.
Selecting Security Vendors
Security threats can evolve quickly and network managers need solutions to combat threats. We asked WAN managers about their strategy for sourcing security solutions.
What best describes your WAN security sourcing strategy?
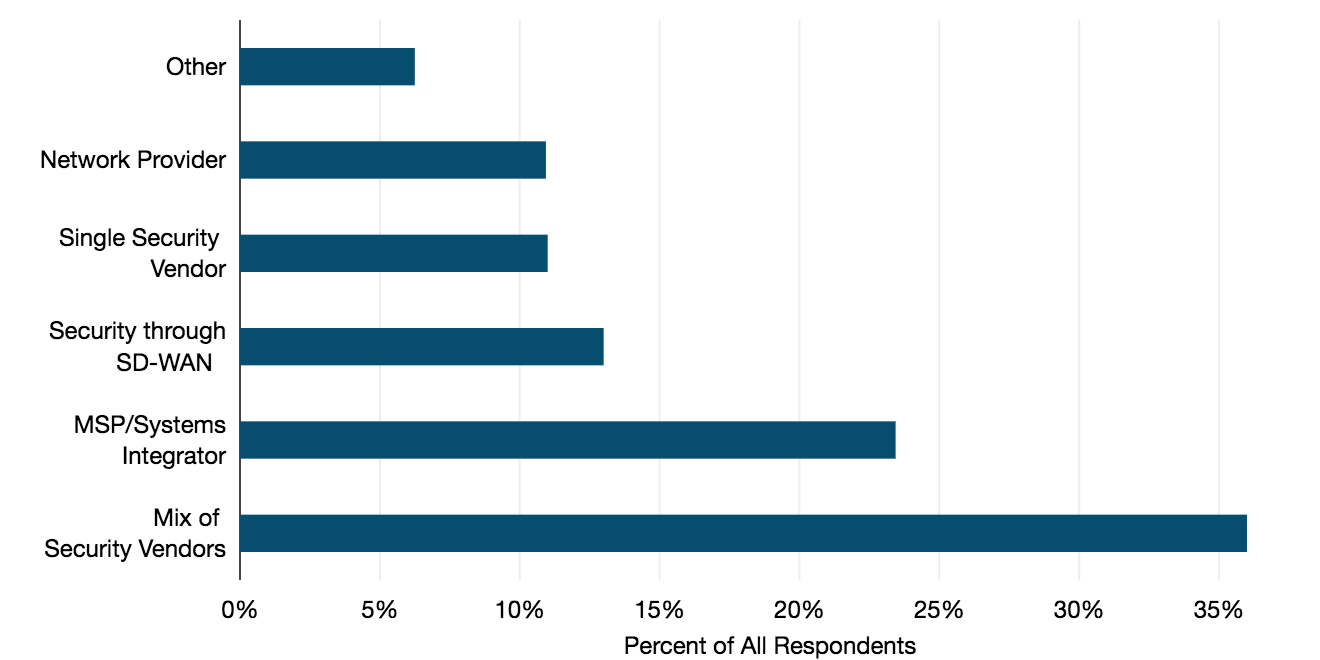
Over one-third said they are using a mix of security vendors.
A common rationale was that, because the security landscape moves quickly as threats evolve, it can be better to evaluate vendor solutions on a piecemeal basis rather than committing to one solution. You can drop a vendor if their solution becomes ineffective and adopt another one just as quickly.
Just under one-quarter of participating companies sourced their network security through a managed service provider (MSP) or a systems integrator.
Sourcing through a single security vendor, an MSP, or integrated into an SD-WAN service, either as a built-in proprietary feature or through the vendor’s channel partner, were each chosen by around one-tenth of respondents.
As SD-WAN adoption rises and ZTS become more ubiquitous, we’ll be keeping an eye on how the network security landscape shifts. (Perhaps in the form of a more detailed network security vendor research product? Watch this space to find out.)
Elizabeth Thorne
Elizabeth Thorne was formerly a Senior Research Analyst at TeleGeography. Her work was focused on enterprise network research.