While the key SD-WAN transformation use case was built around network cost and resiliency, its focus is now shifting to security.
Enterprises have moved to more internet connectivity. Traffic patterns have moved away from on-premise data centers to neutral colo facilities or cloud service providers/hyperscalers. And over the past two years, edge access has moved out of the corporate site—to home and remote connections.
These forces changed how enterprises approach network security, and SD-WAN vendors have responded with new partnerships and feature sets.
This review looks at enterprise security trends and how SD-WAN vendors have adapted to accommodate security needs.
Security Approaches
How are SD-WAN vendors approaching integrating security features into their services?
Many are content to rely on third-party security suppliers or allow customers to bring their own firewall.
In 2021, Zscaler and Palo Alto Networks were cited the most as security partners among the SD-WAN vendors we profile. Check Point, Symantec, and WatchGuard were also in the mix.
SD-WAN Security Partnerships, 2021
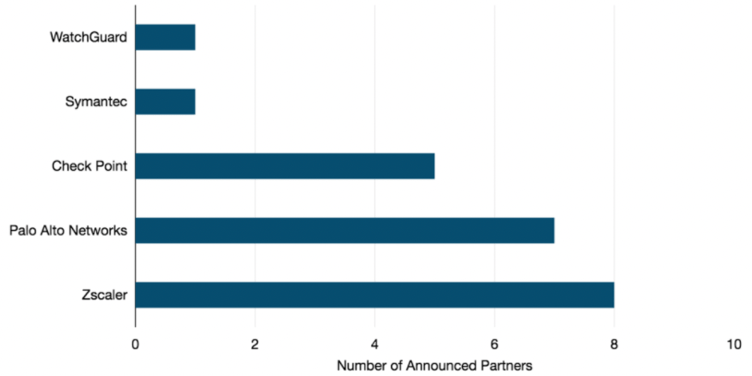
It is worth noting that some of the most familiar names in the security space are missing from the figure above. These companies—such as Cisco, Fortinet, and Barracuda Networks—have leveraged their in-house security expertise and integrated it into their own SD-WAN service.
They tend to partner with carriers and managed SD-WAN service providers—rather than other SD-WAN vendors—to help them with their security portfolios.
Suppliers such as CATO Networks run secure SD-WAN as a service. This incorporates integrated security and SD-WAN over its own private backbone network.
Telcos already have a host of network security services in their portfolio. Opting for a managed service outsources the burden of securing the network to your carrier.
On-premise vs. Cloud-based Security Services
One of the most common security questions we’ve heard from enterprises is whether to opt for a hardware-based or a cloud-based security service.
Currently, a majority of the WAN managers in our survey report that they utilize a hardware-based approach (approximately 75%). In comparison, just over one-in-four respondents reported using software/cloud-based security for securing internet traffic.
Each approach is unique, and there are pros and cons to both.
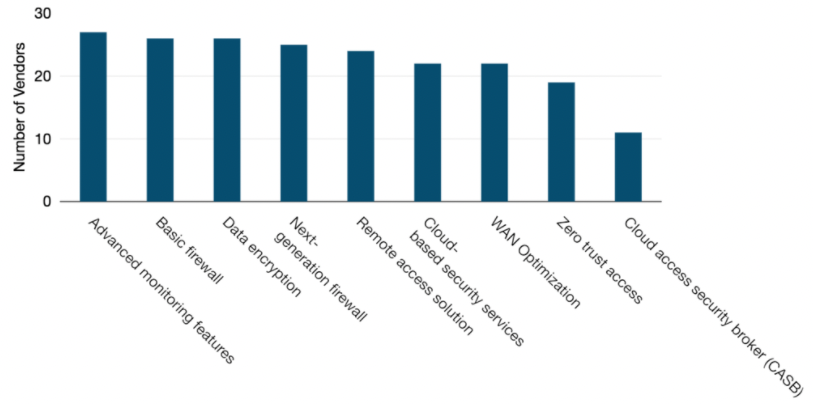
On-premise security services are available from almost all SD-WAN vendors. Looking at the figure below, 26 of our 27 profiled SD-WAN vendors incorporated hardware-based security such as a traditional firewall as part of their service.
While offered by a smaller number of vendors, cloud-based security is an increasingly popular approach to deliver security features across the network. Of the 27 profiled SD-WAN vendors, 22 indicated that they now offered the service in this manner.
Available SD-WAN Service Features, 2021
The answer to which security approach is the best is often an unsatisfying “it depends.”
For many enterprises, the best approach may actually be a hybrid solution. Specifically, a mix of on-premise next generation firewalls and UTM alongside a cloud-based security service with zero trust access.
This approach would not only secure local internet breakouts and branch offices, but also allow security policies to follow mobile employees as needed.
Zero Trust Access
With the shift in the network security landscape, customer mindsets have moved from “trust but verify” to “never trust, always verify.”
This second approach has been branded as “Zero Trust” security and focuses on verifying users, validating devices, limiting access and privileges, and using analytics to adapt policies.
Interest among enterprise customers is high, and many SD-WAN vendors now incorporate the approach into their SD-WAN overlays.
Brianna Boudreau
Senior Research Manager Brianna Boudreau joined TeleGeography in 2008. She specializes in pricing and market analysis for wholesale and enterprise network services with a regional focus on Asia and Oceania. While at TeleGeography, Brianna has helped develop and launch several new lines of research, including our Cloud and WAN Research Service.




